IP addressing is the backbone of network communication, enabling devices to identify and locate each other on a network. Understanding IP addresses, both IPv4 and IPv6, is crucial for ethical hackers to effectively analyze network traffic, identify vulnerabilities, and perform penetration testing. This lesson will delve into the structure, function, and significance of these addressing schemes, providing the foundational knowledge needed for subsequent topics like network scanning and reconnaissance.
IPv4 Addressing: A Deep Dive
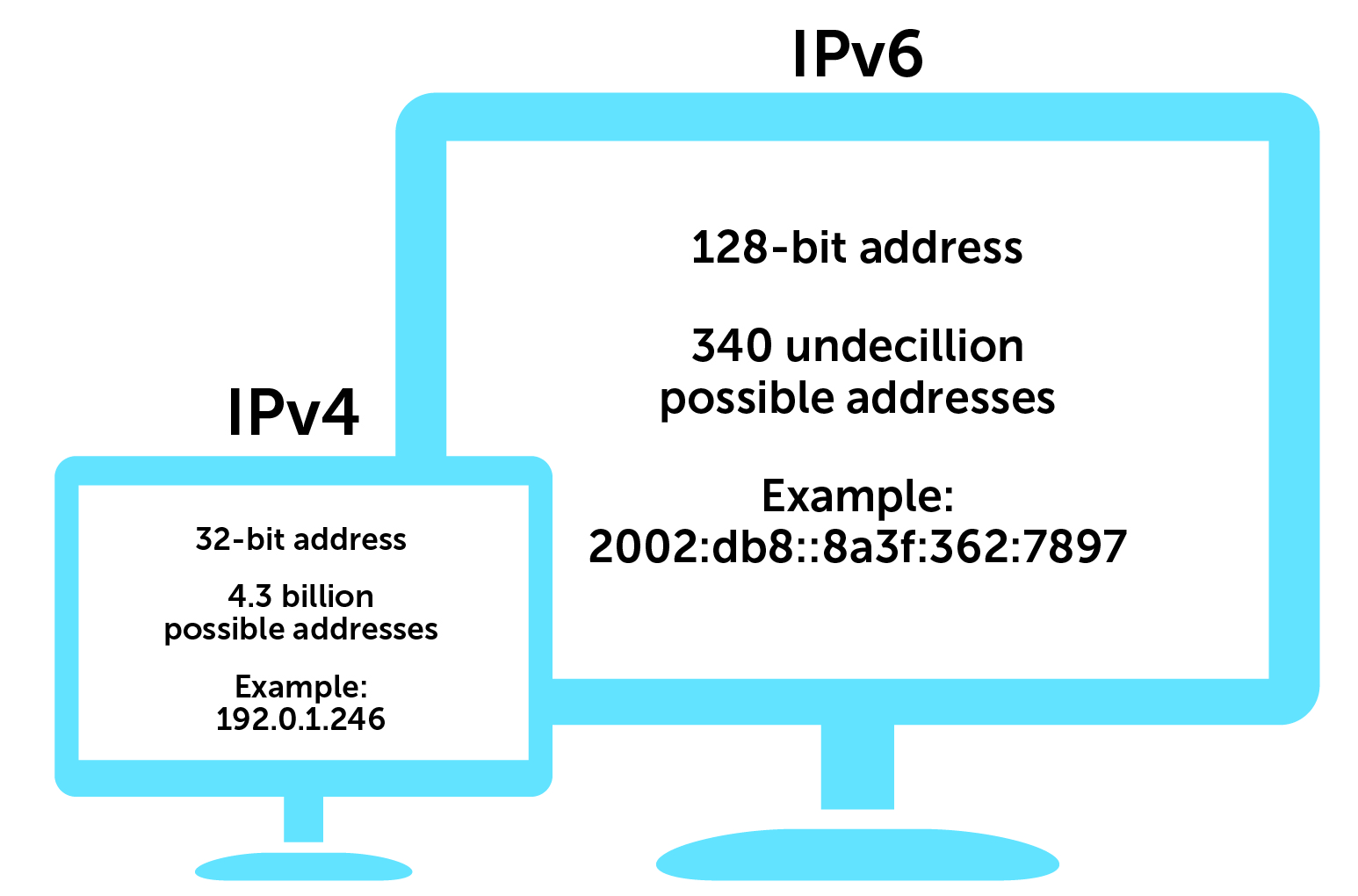
IPv4 (Internet Protocol version 4) is the fourth version of the Internet Protocol, and it’s one of the core protocols of standards-based internetworking methods in the Internet and other packet-switched networks. IPv4 uses a 32-bit address space, which allows for approximately 4.3 billion unique addresses.
Structure of an IPv4 Address
An IPv4 address is represented in dotted decimal notation, consisting of four octets (8-bit bytes) separated by periods. Each octet represents a decimal number between 0 and 255. For example, 192.168.1.1 is a valid IPv4 address.
IPv4 Address Classes
Historically, IPv4 addresses were divided into classes (A, B, C, D, and E) based on the first octet of the address. While classful addressing is largely obsolete, understanding the concept is helpful for historical context and recognizing certain address ranges.
- Class A: Addresses from
1.0.0.0to126.0.0.0. The first octet identifies the network, and the remaining three octets identify the host within that network. Class A networks can support a large number of hosts. - Class B: Addresses from
128.0.0.0to191.255.0.0. The first two octets identify the network, and the remaining two octets identify the host. Class B networks support a moderate number of hosts. - Class C: Addresses from
192.0.0.0to223.255.255.0. The first three octets identify the network, and the last octet identifies the host. Class C networks support a small number of hosts. - Class D: Addresses from
224.0.0.0to239.255.255.255. These addresses are used for multicast traffic. - Class E: Addresses from
240.0.0.0to255.255.255.255. These addresses are reserved for experimental purposes.
Public vs. Private IPv4 Addresses
IPv4 addresses are categorized as either public or private.
- Public IP Addresses: These addresses are globally unique and are assigned to organizations by Internet Assigned Numbers Authority (IANA) and Regional Internet Registries (RIRs). Public IP addresses are used for communication over the public internet. Example: A web server hosting a website needs a public IP address to be accessible from anywhere in the world.
- Private IP Addresses: These addresses are reserved for use within private networks, such as home networks or corporate networks. Private IP addresses are not routable on the public internet. The following ranges are reserved for private addressing:
10.0.0.0–10.255.255.255(10/8 prefix)172.16.0.0–172.31.255.255(172.16/12 prefix)192.168.0.0–192.168.255.255(192.168/16 prefix) Example: A home router typically assigns private IP addresses (e.g.,192.168.1.100) to devices connected to the local network.
Network Address Translation (NAT)
Since private IP addresses are not routable on the internet, Network Address Translation (NAT) is used to allow devices on a private network to communicate with the internet using a single public IP address. NAT translates the private IP addresses of devices on the private network to the public IP address of the router or gateway.
Example: When a computer on a home network (using a private IP address) sends a request to a website, the router translates the computer’s private IP address to its own public IP address before sending the request to the internet. When the response comes back, the router translates the destination IP address back to the computer’s private IP address.
Subnetting and CIDR Notation
Subnetting is the process of dividing a network into smaller, more manageable subnetworks. This is done by borrowing bits from the host portion of the IP address and using them to create network addresses. Classless Inter-Domain Routing (CIDR) notation is used to represent the network address and the number of bits used for the network prefix.
CIDR notation is represented as IP address/prefix length. The prefix length indicates the number of bits in the IP address that are used for the network address. For example, 192.168.1.0/24 indicates that the first 24 bits of the IP address (192.168.1) represent the network address, and the remaining 8 bits represent the host address.
Example: Consider the IP address 192.168.1.10/24. The /24 indicates that the network address is 192.168.1.0, and the host address is 10. This means that all devices with IP addresses in the range 192.168.1.1 to 192.168.1.254 are on the same network.
Special IPv4 Addresses
Certain IPv4 addresses have special meanings:
- 0.0.0.0: Represents the current network. It’s often used during DHCP address allocation.
- 255.255.255.255: Represents the broadcast address for the current network.
- 127.0.0.1: Represents the loopback address, used for testing network configurations on the local machine. Any traffic sent to this address is looped back to the sending device.
- 169.254.0.0/16: This is the Automatic Private IP Addressing (APIPA) range. Devices use this range when they fail to obtain an IP address from a DHCP server.
IPv6 Addressing: The Next Generation
IPv6 (Internet Protocol version 6) is the latest version of the Internet Protocol, designed to address the limitations of IPv4, particularly the exhaustion of IPv4 addresses. IPv6 uses a 128-bit address space, which allows for approximately 3.4 x 10^38 unique addresses, a vastly larger address space than IPv4.
Structure of an IPv6 Address
An IPv6 address is represented in hexadecimal notation, consisting of eight groups of four hexadecimal digits, separated by colons. For example, 2001:0db8:85a3:0000:0000:8a2e:0370:7334 is a valid IPv6 address.
IPv6 Address Compression
To simplify IPv6 addresses, two compression rules are used:
- Leading Zeroes: Leading zeroes within each group of four hexadecimal digits can be omitted. For example,
2001:0db8:0000:0000:0000:0000:0000:0001can be written as2001:db8:0:0:0:0:0:1. - Consecutive Zero Groups: One or more consecutive groups of zeroes can be replaced with a double colon (
::). This can only be done once in an address. For example,2001:db8:0:0:0:0:0:1can be further compressed to2001:db8::1.
Example: The address 2001:0db8:85a3:0000:0000:8a2e:0370:7334 can be compressed to 2001:db8:85a3::8a2e:370:7334.
IPv6 Address Types
IPv6 defines several address types:
- Unicast Addresses: Identify a single interface. Packets sent to a unicast address are delivered to that specific interface.
- Global Unicast Addresses: These are routable on the internet and are similar to public IPv4 addresses. They typically start with
2000::/3. Example:2001:db8:1234:5678::1is a global unicast address. - Link-Local Addresses: These are used for communication within a single network segment (link). They are automatically configured on interfaces and start with
fe80::/10. Example:fe80::a8bb:ccff:fe00:1234is a link-local address. - Unique Local Addresses (ULA): These are similar to private IPv4 addresses and are used for communication within a private network. They start with
fd00::/8. Example:fd00::1:2:3:4is a unique local address.
- Global Unicast Addresses: These are routable on the internet and are similar to public IPv4 addresses. They typically start with
- Multicast Addresses: Identify a group of interfaces. Packets sent to a multicast address are delivered to all interfaces in the group. They start with
ff00::/8. Example:ff02::1is the all-nodes multicast address, which is used to send packets to all devices on the local network. - Anycast Addresses: Identify a group of interfaces, but packets sent to an anycast address are delivered to the nearest interface in the group, as determined by routing protocols.
IPv6 Address Autoconfiguration
IPv6 supports stateless address autoconfiguration (SLAAC), which allows devices to automatically configure their IPv6 addresses without the need for a DHCP server. In SLAAC, a device sends a Router Solicitation (RS) message to the all-routers multicast address (ff02::2). A router on the network responds with a Router Advertisement (RA) message, which contains the network prefix and other configuration information. The device then uses this information to generate its own IPv6 address.
Example: A laptop connecting to a new IPv6 network will send an RS message. A router on the network will respond with an RA message containing the network prefix (e.g., 2001:db8:1234:5678::/64). The laptop will then generate its own IPv6 address by combining the network prefix with a unique interface identifier (e.g., derived from its MAC address).
IPv6 Extension Headers
IPv6 uses extension headers to provide additional functionality, such as fragmentation, security, and routing options. Extension headers are added after the main IPv6 header and can be chained together to provide multiple options.
Example: The Authentication Header (AH) and Encapsulating Security Payload (ESP) headers are used to provide security services in IPv6.
Comparing IPv4 and IPv6
| Feature | IPv4 | IPv6 |
|---|---|---|
| Address Length | 32 bits | 128 bits |
| Address Space | ~4.3 billion addresses | ~3.4 x 10^38 addresses |
| Address Notation | Dotted decimal | Hexadecimal with colons |
| Header Size | 20 bytes (without options) | 40 bytes |
| Address Types | Unicast, Broadcast, Multicast | Unicast, Multicast, Anycast |
| Autoconfiguration | Requires DHCP | Stateless Address Autoconfiguration (SLAAC) |
| Security | Relies on IPsec for security | Built-in security features (IPsec optional) |
| Fragmentation | Can be done by sender or routers | Done only by sender |
Practical Exercises
- IPv4 Address Identification: Given the IP address
172.20.5.15/16, identify the network address, host address, and the number of usable host addresses in the network. - IPv6 Address Compression: Compress the following IPv6 address:
2001:0db8:0000:0000:0000:ff00:0042:8329. - Public vs. Private IP: Explain the difference between a public and private IP address. Give an example of when each would be used.
- IPv6 Autoconfiguration: Describe the process of IPv6 stateless address autoconfiguration (SLAAC). What messages are exchanged, and what information is contained in those messages?
Real-World Application
Consider a scenario where a company is migrating its network from IPv4 to IPv6. The company has a web server that needs to be accessible from both IPv4 and IPv6 clients. To achieve this, the company can use a dual-stack configuration, where the web server has both an IPv4 address and an IPv6 address. This allows clients to connect to the web server using either protocol.
The company also needs to ensure that its internal network is secure. To do this, they can use IPv6 firewalls to filter traffic based on IPv6 addresses and extension headers. They can also use IPsec to encrypt traffic between different parts of the network.
Furthermore, the company can leverage IPv6’s autoconfiguration capabilities to simplify network management. Devices can automatically configure their IPv6 addresses without the need for a DHCP server, reducing the administrative overhead.
In the context of ethical hacking, understanding this dual-stack environment is crucial. An ethical hacker would need to assess the security of both the IPv4 and IPv6 configurations, looking for vulnerabilities in each protocol. They would also need to understand how the two protocols interact to identify potential attack vectors. For example, an attacker might try to exploit a vulnerability in the IPv4 configuration to gain access to the IPv6 network, or vice versa.
This lesson has provided a comprehensive overview of IP addressing, covering both IPv4 and IPv6. You’ve learned about the structure of IP addresses, the different address types, and the key differences between IPv4 and IPv6. You’ve also explored practical examples of how IP addressing is used in real-world networks.
Next steps involve delving into common network protocols like HTTP, HTTPS, DNS, and SMTP, which rely heavily on IP addressing for communication. Understanding these protocols will further enhance your ability to analyze network traffic and identify vulnerabilities.