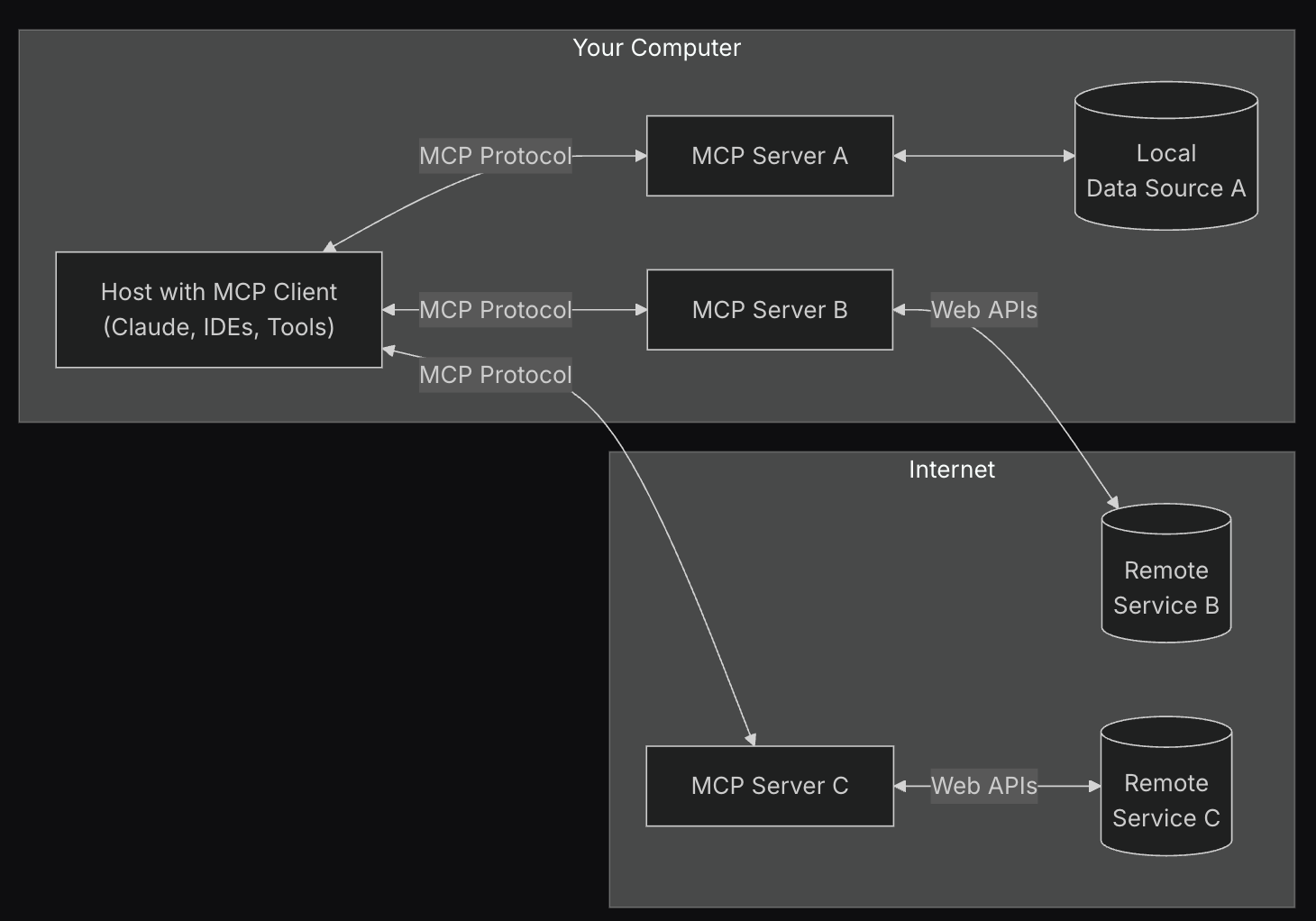
The Ethical Hacker’s Code of Ethics and Legal Considerations
The ethical hacker’s role is critical in safeguarding digital assets, but this role comes with significant responsibilities. Understanding and adhering to a strict code of ethics and being aware of…
The Ultimate Guide to the Best Contract Management Platforms in 2025
Contract management is a critical business function that ensures efficiency, compliance, and risk mitigation. With the rise of digital solutions, companies now have access to powerful platforms that automate and…
Understanding the CIA Triad: Confidentiality, Integrity, and Availability
The CIA Triad – Confidentiality, Integrity, and Availability – forms the cornerstone of information security. It’s a model designed to guide policies for information security within an organization. Understanding these…
What is Cybersecurity and Why is it Important?
Cybersecurity is no longer just a concern for large corporations or government agencies. In our increasingly interconnected world, it’s a fundamental requirement for individuals, small businesses, and critical infrastructure alike.…