U.S. Crypto Law: The GENIUS Act Unveiled
What Is the GENIUS Act? The GENIUS Act—short for Guiding and Establishing National Innovation for U.S. Stablecoins Act—represents the first comprehensive federal legislation for stablecoins in the United States. It…
Active Reconnaissance: Techniques for Direct Information Gathering
Active reconnaissance is a crucial step in ethical hacking and cybersecurity. Unlike passive reconnaissance, which relies on publicly available information, active reconnaissance involves directly interacting with the target system to…
Passive Reconnaissance: Gathering Information from Public Sources
Passive reconnaissance is the initial phase of information gathering in ethical hacking and cybersecurity. It involves collecting information about a target without directly interacting with their systems. This approach minimizes…
Hands-on: Basic Network Scanning with Nmap
Nmap is a cornerstone tool for network administrators and ethical hackers alike. It allows you to discover hosts and services on a computer network by sending packets and analyzing the…
Introduction to Network Scanning Tools: Nmap
Network scanning is a fundamental skill for ethical hackers. It allows you to discover hosts and services on a network, which is the first step in identifying potential vulnerabilities. Nmap…
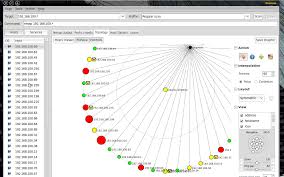
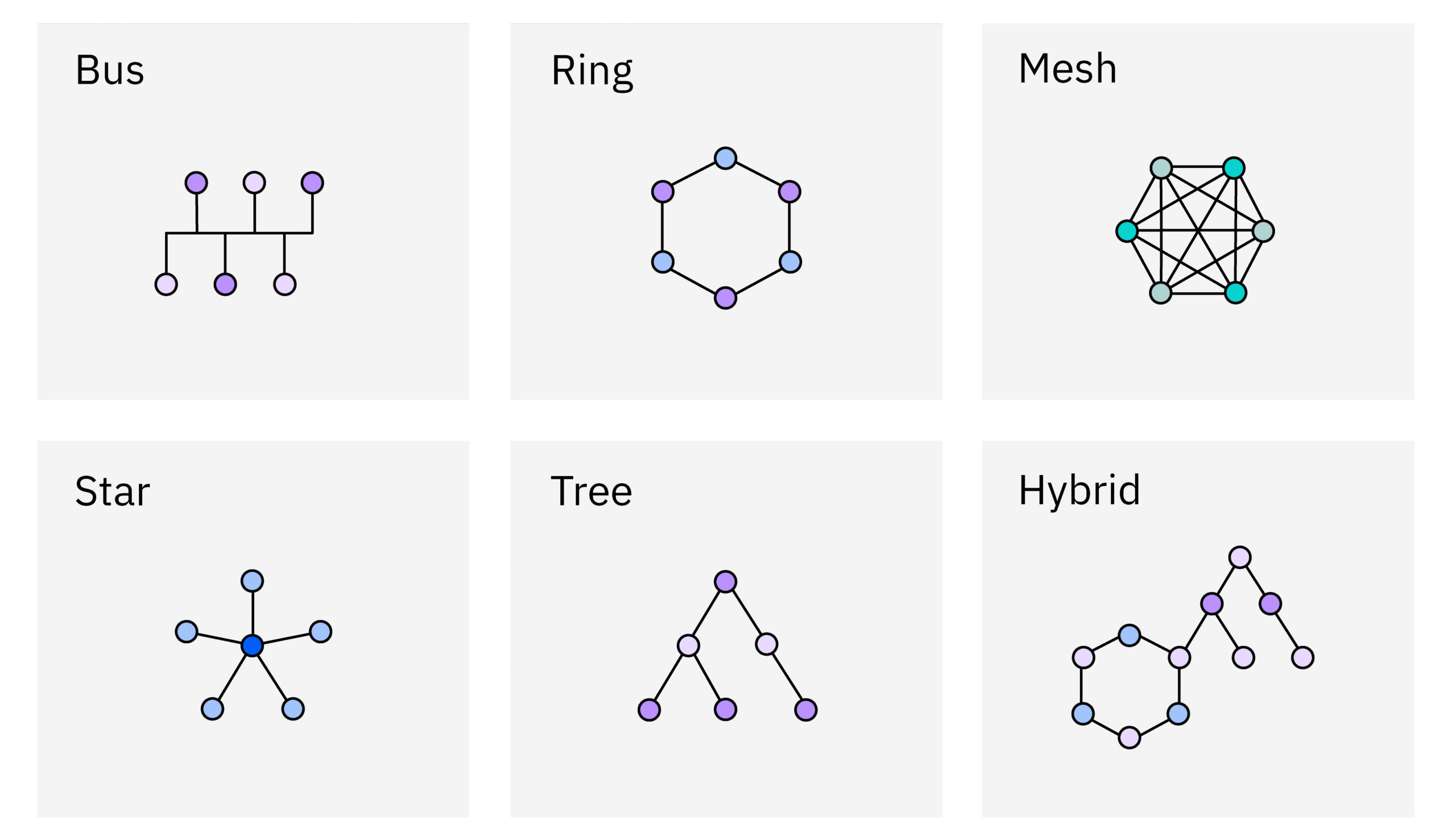
Network Topologies and Architectures
Network topologies and architectures are the fundamental building blocks of any network infrastructure. Understanding these concepts is crucial for ethical hackers as it allows them to visualize the network’s structure,…
Common Network Protocols: HTTP, HTTPS, DNS, SMTP
Understanding network protocols is crucial for ethical hackers. These protocols are the languages that devices use to communicate, and knowing how they work allows you to identify vulnerabilities and potential…
Introduction to Networking Concepts: TCP/IP Model, OSI Model
Networking is the backbone of modern communication and a critical area for ethical hackers to understand. A solid grasp of networking concepts allows you to identify vulnerabilities, analyze network traffic,…
Setting up a Virtual Lab Environment for Ethical Hacking
Setting up a virtual lab environment is a crucial first step in learning ethical hacking. It provides a safe and isolated space to experiment with tools and techniques without risking…
Common Cybersecurity Threats: Malware, Phishing, and Social Engineering
Malware, phishing, and social engineering represent some of the most pervasive and dangerous threats in the cybersecurity landscape. Understanding how these attacks work, how to recognize them, and how to…