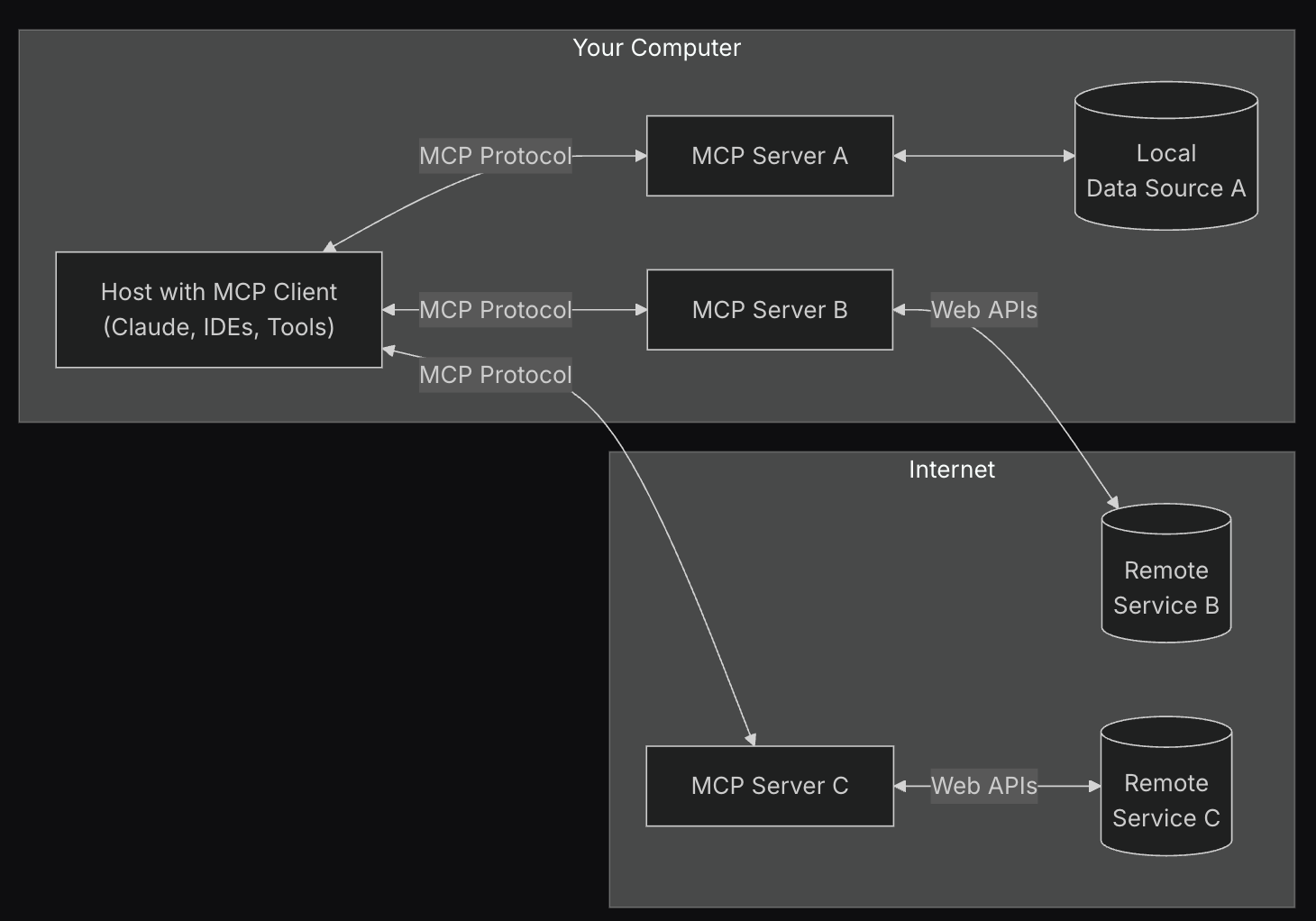
The Best Crypto Exchanges in 2025: Pioneering the Future of Digital Finance
The cryptocurrency landscape in 2025 is a dynamic fusion of innovation, regulation, and user-centric design. As blockchain technology matures and global adoption surges, crypto exchanges have evolved beyond mere trading…