U.S. Crypto Law: The GENIUS Act Unveiled
What Is the GENIUS Act? The GENIUS Act—short for Guiding and Establishing National Innovation for U.S. Stablecoins Act—represents the first comprehensive federal legislation for stablecoins in the United States. It…
Getting Started with Bitcoin
Bitcoin is a revolutionary system that is quite complex and has a steep learning curve. Make sure you have a decent grasp of the system before you store a significant…
How to Read a Crypto Heat Map and Trade Futures & Options
Cryptocurrency trading has evolved beyond simple spot trading, with derivatives like futures and options gaining popularity. To make informed decisions, traders often use tools like crypto heat maps, which provide a…
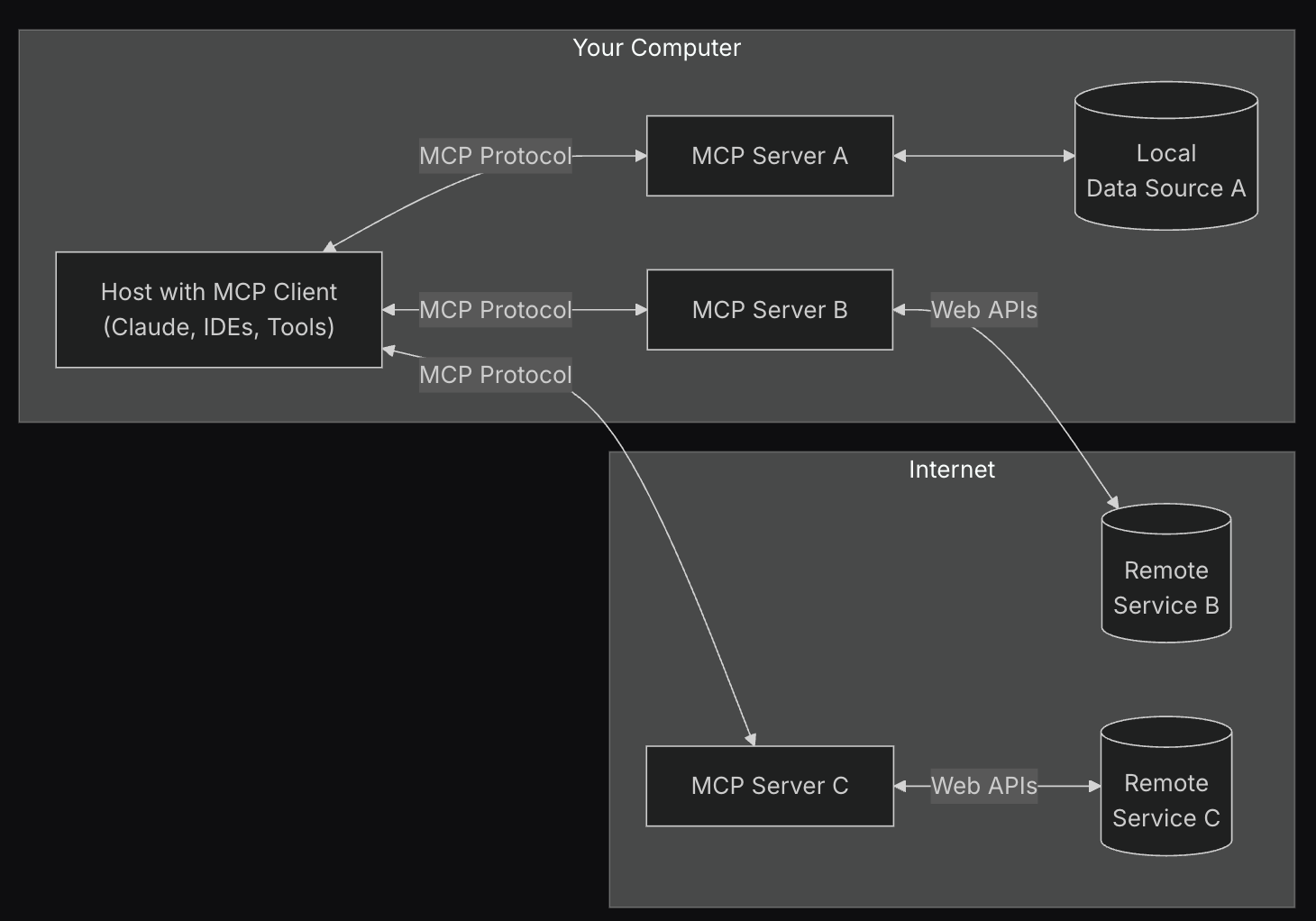
Introduction to Networking Concepts: TCP/IP Model, OSI Model
Networking is the backbone of modern communication and a critical area for ethical hackers to understand. A solid grasp of networking concepts allows you to identify vulnerabilities, analyze network traffic,…
MEXC Lists Doodles (DOOD) with 50,000 USDT Worth of DOOD and 50,000 USDT Bonus Prize Pool
The cryptocurrency exchange MEXC has made waves in the Web3 space with its May 9, 2025, listing of Doodles (DOOD), the native token of the beloved NFT-turned-entertainment brand Doodles. This move…
Setting up a Virtual Lab Environment for Ethical Hacking
Setting up a virtual lab environment is a crucial first step in learning ethical hacking. It provides a safe and isolated space to experiment with tools and techniques without risking…
Common Cybersecurity Threats: Malware, Phishing, and Social Engineering
Malware, phishing, and social engineering represent some of the most pervasive and dangerous threats in the cybersecurity landscape. Understanding how these attacks work, how to recognize them, and how to…
The Ultimate Guide to the Best Contract Management Platforms in 2025
Contract management is a critical business function that ensures efficiency, compliance, and risk mitigation. With the rise of digital solutions, companies now have access to powerful platforms that automate and…
The Future of Ethereum (ETH): What to Expect in the Coming Years
Ethereum (ETH) has long been the backbone of decentralized applications (dApps), smart contracts, and the booming decentralized finance (DeFi) ecosystem. As the second-largest cryptocurrency by market capitalization, Ethereum continues to…
Stablecoins Steal the Spotlight: How Tether and USDT Are Now Driving Bitcoin’s Price, Says MEXC Executive
The narrative around Bitcoin’s price volatility has long centered on retail investor sentiment, hype cycles, and macroeconomic trends. But in a surprising pivot, Matthew Lee, COO of crypto exchange MEXC,…