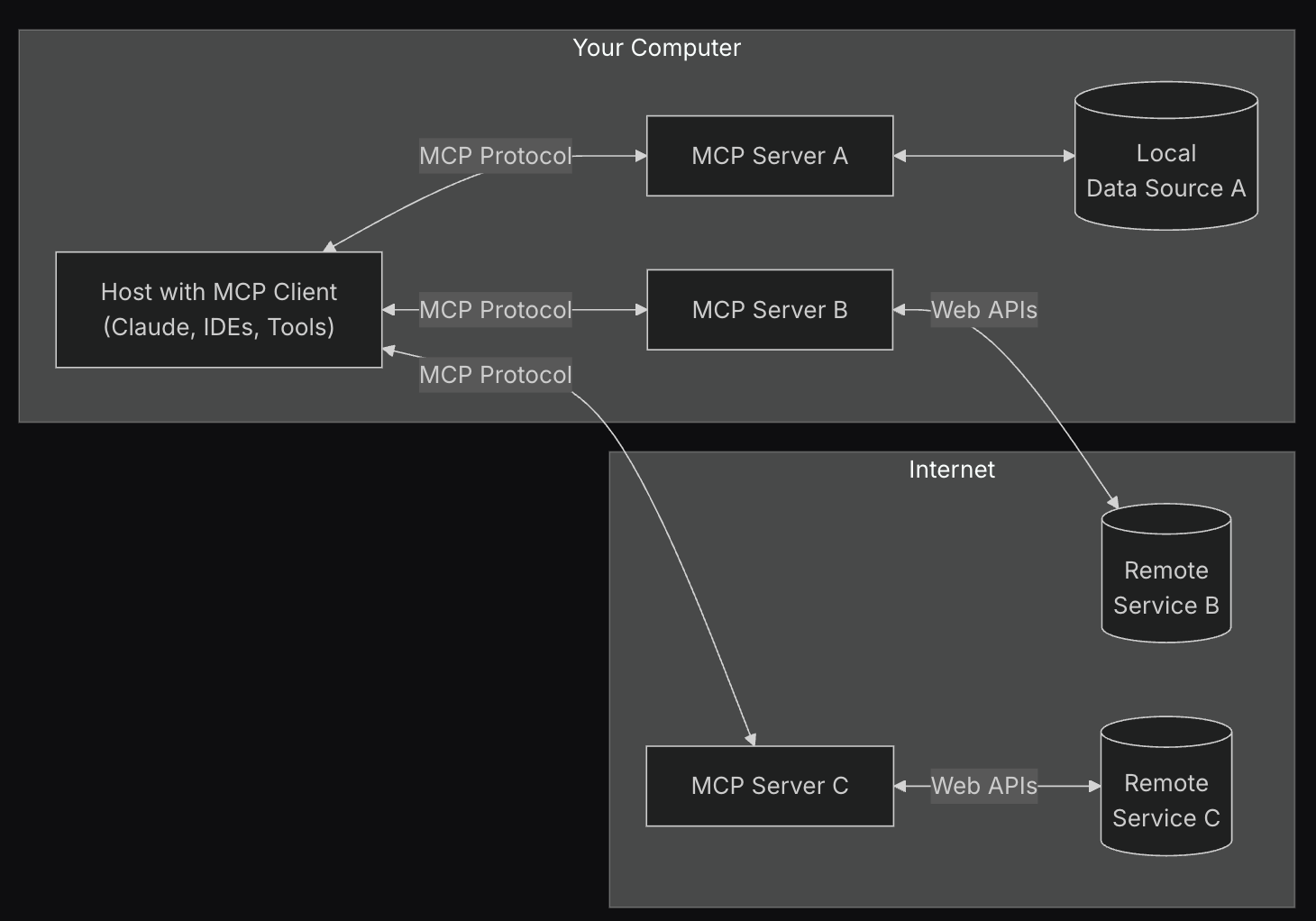
The Ultimate Guide to the Best Contract Management Platforms in 2025
Contract management is a critical business function that ensures efficiency, compliance, and risk mitigation. With the rise of digital solutions, companies now have access to powerful platforms that automate and…