Network topologies and architectures are the fundamental building blocks of any network infrastructure. Understanding these concepts is crucial for ethical hackers as it allows them to visualize the network’s structure, identify potential vulnerabilities, and plan effective attacks or defenses. This knowledge enables you to analyze traffic flow, pinpoint critical assets, and understand how different components interact, ultimately leading to a more comprehensive security assessment.
Network Topologies
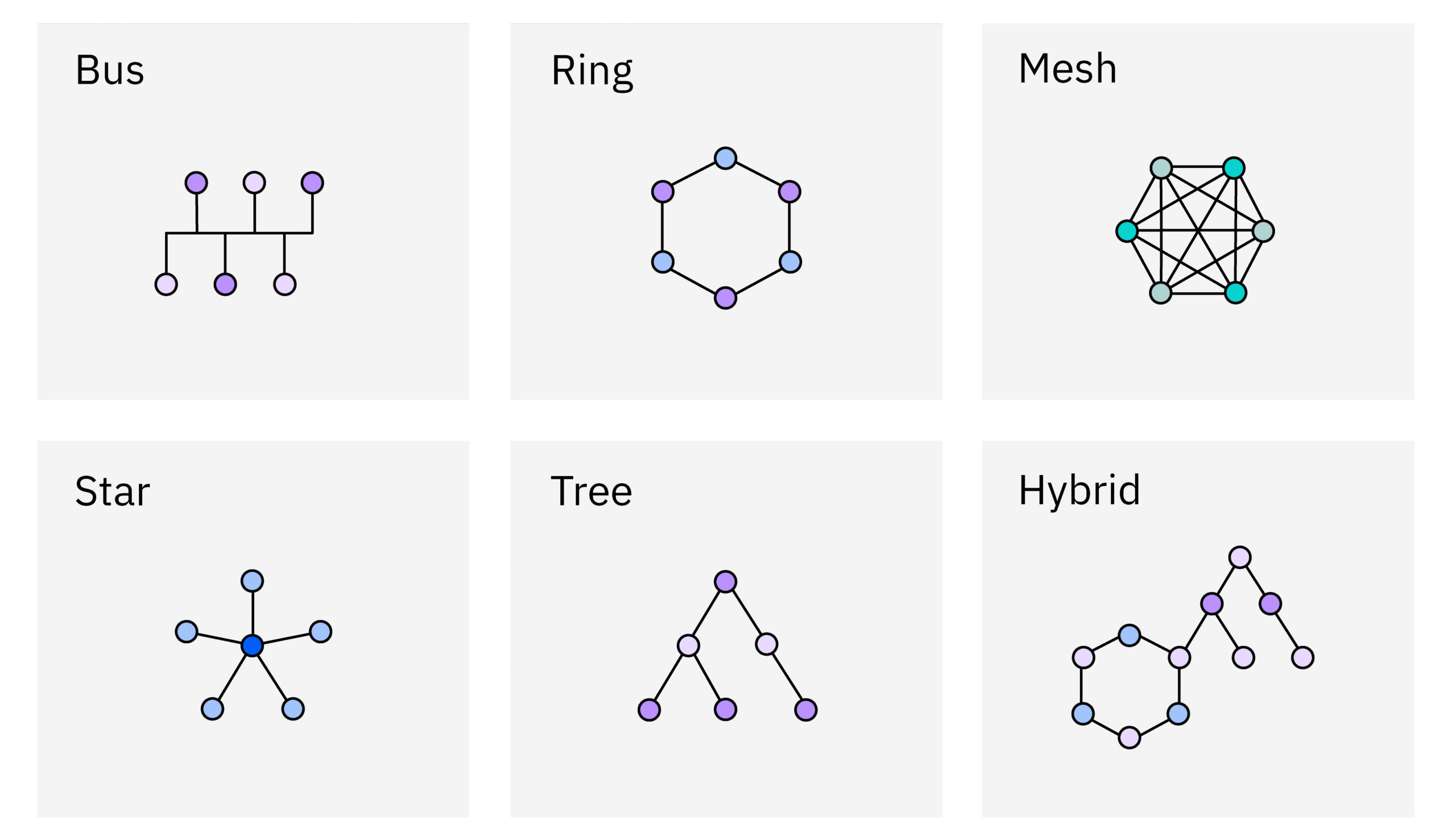
A network topology defines the physical or logical arrangement of devices in a network. It describes how devices are connected and how data is transmitted between them. Choosing the right topology depends on factors like cost, scalability, reliability, and security requirements.
Bus Topology
In a bus topology, all devices are connected to a single cable, called the bus or backbone. Data is transmitted along the bus, and all devices can “see” the data, but only the device with the matching address processes it.
- Advantages: Simple to implement and relatively inexpensive for small networks.
- Disadvantages:
- Single point of failure: If the bus cable breaks, the entire network goes down.
- Limited scalability: Adding more devices can degrade performance due to increased traffic and collisions.
- Security concerns: All devices see all traffic, making it easier to eavesdrop.
Example: Imagine a small office where all computers are connected to a single Ethernet cable running along the wall. If one computer sends a message, all other computers on the cable “hear” it, but only the intended recipient processes it.
Hypothetical Scenario: A small startup uses a bus topology for its internal network. An attacker gains access to one computer on the bus and can potentially sniff all network traffic, including sensitive data being transmitted between other computers.
Ring Topology
In a ring topology, each device is connected to exactly two other devices, forming a closed loop. Data travels in one direction around the ring, with each device acting as a repeater to forward the data to the next device.
- Advantages:
- Relatively simple to implement.
- Data collisions are minimized because data travels in one direction.
- Disadvantages:
- Single point of failure: If one device or cable breaks, the entire network can go down.
- Difficult to troubleshoot: Identifying the source of a problem can be challenging.
- Adding or removing devices can disrupt the network.
Example: Consider a network of sensors in a factory, where each sensor is connected to two neighboring sensors, forming a ring. Data from each sensor is passed along the ring until it reaches a central control system.
Hypothetical Scenario: An attacker targets a single node in a ring network used for critical infrastructure monitoring. By compromising that node, the attacker can disrupt the flow of data and potentially cause a system failure.
Star Topology
In a star topology, all devices are connected to a central hub or switch. All data transmitted between devices must pass through the central device.
- Advantages:
- Easy to troubleshoot: Problems can be easily isolated to a specific device or cable.
- Scalable: Adding or removing devices is relatively easy without disrupting the entire network.
- More resilient: If one device or cable fails, it does not affect the rest of the network.
- Disadvantages:
- Central point of failure: If the central hub or switch fails, the entire network goes down.
- More expensive: Requires a central device (hub or switch) and more cabling than bus or ring topologies.
Example: Most modern home and office networks use a star topology, with all devices connected to a central router or switch.
Hypothetical Scenario: An attacker launches a denial-of-service (DoS) attack against the central switch in a star network. By overwhelming the switch with traffic, the attacker can disrupt communication between all devices on the network.
Mesh Topology
In a mesh topology, each device is connected to multiple other devices. There are two types of mesh topologies:
- Full Mesh: Every device is directly connected to every other device in the network.
- Partial Mesh: Some devices are connected to all other devices, while others are only connected to a few.
- Advantages:
- Highly resilient: Multiple paths between devices provide redundancy and fault tolerance.
- Improved performance: Data can be transmitted along the most efficient path.
- Disadvantages:
- Expensive: Requires a large amount of cabling and network interfaces.
- Complex to implement and manage.
Example: The internet backbone uses a mesh topology to ensure high availability and reliability. If one path between two points fails, data can be rerouted along another path.
Hypothetical Scenario: An attacker attempts to disrupt communication between two critical servers in a mesh network. However, due to the redundant connections, data can still be transmitted along alternative paths, minimizing the impact of the attack.
Tree Topology
A tree topology combines characteristics of bus and star topologies. It consists of a hierarchy of devices, with a central root node connected to multiple branches, which in turn are connected to other devices.
- Advantages:
- Scalable: Easy to expand by adding new branches.
- Hierarchical management: Easier to manage and control the network.
- Disadvantages:
- Central point of failure: If the root node fails, the entire network goes down.
- More complex than star or bus topologies.
Example: A large corporate network might use a tree topology, with a central data center connected to multiple branch offices, each of which has its own local network.
Hypothetical Scenario: An attacker targets the root server in a tree topology network. By compromising the root server, the attacker can potentially gain control over the entire network infrastructure.
Network Architectures
Network architecture refers to the overall design and structure of a network, including the hardware, software, protocols, and services used to create and manage the network. Different architectures are suited for different purposes, depending on factors like size, security requirements, and performance needs.
Client-Server Architecture
In a client-server architecture, one or more clients request services from a central server. The server provides resources, such as files, databases, or applications, to the clients.
- Advantages:
- Centralized management: Easier to manage and control resources.
- Improved security: Security policies can be enforced centrally.
- Scalable: Servers can be upgraded or added to handle increased demand.
- Disadvantages:
- Single point of failure: If the server fails, clients cannot access resources.
- Can be expensive: Requires dedicated server hardware and software.
Example: A web server hosting a website is a classic example of a client-server architecture. Clients (web browsers) request web pages from the server, which responds with the requested content.
Hypothetical Scenario: An attacker launches a distributed denial-of-service (DDoS) attack against a web server in a client-server architecture. By overwhelming the server with traffic from multiple sources, the attacker can prevent legitimate clients from accessing the website.
Peer-to-Peer (P2P) Architecture
In a peer-to-peer architecture, all devices (peers) have equal capabilities and can communicate directly with each other without the need for a central server. Each peer can act as both a client and a server.
- Advantages:
- Inexpensive: Does not require dedicated server hardware.
- Resilient: No single point of failure.
- Easy to set up: Simple to configure and deploy.
- Disadvantages:
- Difficult to manage: No central control or security policies.
- Security risks: Each peer is responsible for its own security.
- Performance issues: Performance can degrade as the number of peers increases.
Example: File-sharing networks, such as BitTorrent, are examples of peer-to-peer architectures. Users can download files from and upload files to other users directly.
Hypothetical Scenario: An attacker distributes malware through a peer-to-peer file-sharing network. Users who download infected files can unknowingly spread the malware to other peers on the network.
Cloud Architecture
Cloud architecture refers to the use of cloud computing services to build and deploy applications and services. Cloud providers offer a variety of services, such as compute, storage, and networking, that can be accessed over the internet.
- Advantages:
- Scalable: Resources can be easily scaled up or down as needed.
- Cost-effective: Pay-as-you-go pricing model can reduce costs.
- Reliable: Cloud providers offer high availability and redundancy.
- Disadvantages:
- Security concerns: Data is stored on third-party servers.
- Vendor lock-in: Can be difficult to migrate to another cloud provider.
- Dependence on internet connectivity: Requires a reliable internet connection.
Example: Many organizations use cloud services, such as Amazon Web Services (AWS), Microsoft Azure, or Google Cloud Platform (GCP), to host their websites, applications, and data.
Hypothetical Scenario: An attacker exploits a vulnerability in a cloud provider’s infrastructure to gain access to sensitive data stored by multiple customers. This is a major concern in cloud security, highlighting the importance of robust security measures.
Software-Defined Networking (SDN)
SDN is a network architecture that separates the control plane (which makes decisions about how to route traffic) from the data plane (which forwards traffic). This allows for centralized control and management of the network.
- Advantages:
- Centralized control: Easier to manage and configure the network.
- Programmability: Network behavior can be customized using software.
- Automation: Network tasks can be automated to improve efficiency.
- Disadvantages:
- Complexity: Requires specialized skills and knowledge.
- Security risks: A compromised controller can affect the entire network.
- Vendor lock-in: Can be difficult to migrate to another SDN platform.
Example: Data centers often use SDN to manage their network infrastructure and optimize traffic flow.
Hypothetical Scenario: An attacker gains access to the SDN controller and reprograms the network to redirect traffic to a malicious server. This allows the attacker to intercept sensitive data or launch man-in-the-middle attacks.
Practical Exercises
- Topology Identification: Draw diagrams of the five network topologies discussed (bus, ring, star, mesh, tree). For each topology, list two advantages and two disadvantages.
- Architecture Comparison: Create a table comparing client-server, peer-to-peer, and cloud architectures. Include factors such as cost, scalability, security, and management complexity.
- Scenario Analysis: You are tasked with designing a network for a small office with 10 computers. Which topology would you recommend and why? Consider factors such as cost, scalability, and ease of management.
- Vulnerability Assessment: Research common vulnerabilities associated with each network topology and architecture. For example, what are the common attack vectors against a star topology network?
Real-World Application
Consider a large e-commerce company. They likely use a combination of network topologies and architectures to support their operations.
- Star Topology: Within their corporate offices, they likely use a star topology with switches connecting employee computers to the network.
- Client-Server Architecture: Their website and database servers are likely based on a client-server architecture, with web browsers (clients) requesting data from the servers.
- Cloud Architecture: They might use a cloud provider like AWS or Azure to host their website, store data, and run applications.
- SDN: Their data centers might use SDN to manage network traffic and optimize performance.
Understanding how these different topologies and architectures are used in a real-world scenario can help ethical hackers identify potential vulnerabilities and plan effective security assessments. For example, knowing that the e-commerce company uses a cloud architecture, an ethical hacker would focus on assessing the security of their cloud environment, including access controls, data encryption, and vulnerability management.
In this lesson, we explored various network topologies and architectures, highlighting their advantages, disadvantages, and real-world applications. Understanding these concepts is crucial for ethical hackers as it provides a foundation for analyzing network security and identifying potential vulnerabilities. Building on this knowledge, the next lesson will introduce network scanning tools, such as Nmap, which are used to discover devices and services on a network.