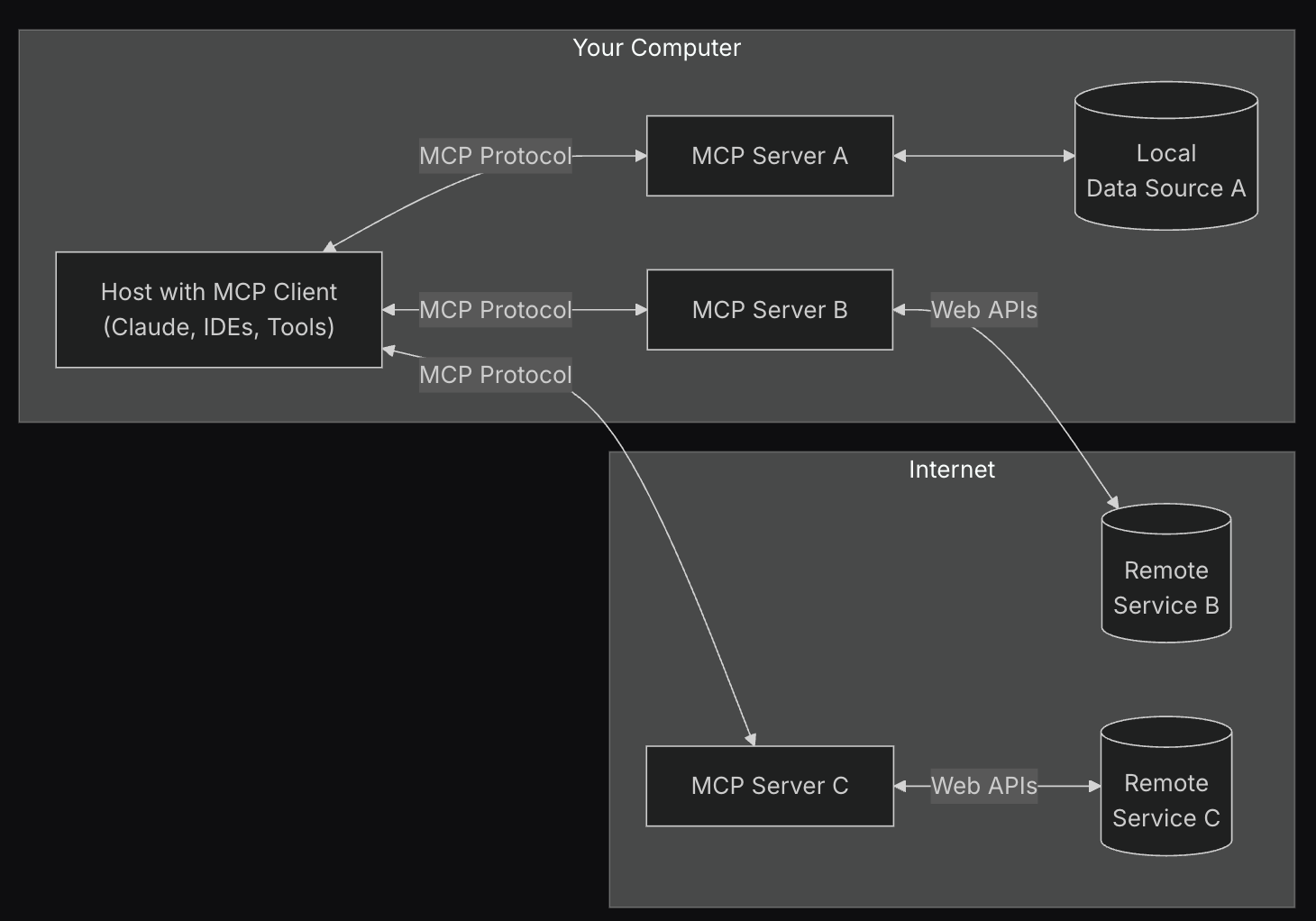
(Beginner-Friendly Learning Path)
Module 1: Introduction to Cybersecurity and Ethical Hacking
| # | Topic | Link |
|---|
| 1 | What is Cybersecurity and Why is it Important? | Start → |
| 2 | Understanding the CIA Triad: Confidentiality, Integrity, and Availability | Start → |
| 3 | Introduction to Ethical Hacking: Definition, Scope, and Benefits | Start → |
| 4 | The Ethical Hacker’s Code of Ethics and Legal Considerations | Start → |
| 5 | Common Cybersecurity Threats: Malware, Phishing, and Social Engineering | Start → |
| 6 | Setting up a Virtual Lab Environment for Ethical Hacking | Start → |
Module 2: Networking Fundamentals for Hackers
| # | Topic | Link |
|---|
| 1 | Introduction to Networking Concepts: TCP/IP Model, OSI Model | Start → |
| 2 | Understanding IP Addressing: IPv4 and IPv6 | Start → |
| 3 | Common Network Protocols: HTTP, HTTPS, DNS, SMTP | Start → |
| 4 | Network Topologies and Architectures | Start → |
| 5 | Introduction to Network Scanning Tools: Nmap | Start → |
| 6 | Hands-on: Basic Network Scanning with Nmap | Start → |
Module 3: Reconnaissance and Information Gathering
| # | Topic | Link |
|---|
| 1 | Passive Reconnaissance: Gathering Information from Public Sources | Start → |
| 2 | Active Reconnaissance: Techniques for Direct Information Gathering | Start → |
| 3 | Using Search Engines and Online Databases for Reconnaissance | Start → |
| 4 | Social Media Reconnaissance: Gathering Information from Social Platforms | Start → |
| 5 | DNS Enumeration: Discovering DNS Records | Start → |
| 6 | Hands-on: Performing Reconnaissance on a Target Website | Start → |
Module 4: Vulnerability Scanning and Analysis
| # | Topic | Link |
|---|
| 1 | Introduction to Vulnerability Scanning: Concepts and Tools | Start → |
| 2 | Understanding Common Vulnerabilities and Exposures (CVEs) | Start → |
| 3 | Using Vulnerability Scanners: Nessus, OpenVAS | Start → |
| 4 | Interpreting Vulnerability Scan Results | Start → |
| 5 | Manual Vulnerability Analysis Techniques | Start → |
| 6 | Hands-on: Scanning a Target System for Vulnerabilities | Start → |
Module 5: Exploitation and Penetration Testing
| # | Topic | Link |
|---|
| 1 | Introduction to Exploitation: Concepts and Techniques | Start → |
| 2 | Understanding Common Exploitation Frameworks: Metasploit | Start → |
| 3 | Exploiting Common Vulnerabilities: SQL Injection, Cross-Site Scripting (XSS) | Start → |
| 4 | Post-Exploitation Techniques: Maintaining Access and Privilege Escalation | Start → |
| 5 | Introduction to Penetration Testing Methodologies | Start → |
| 6 | Hands-on: Exploiting a Vulnerable Web Application | Start → |
Module 6: Password Cracking and Security
| # | Topic | Link |
|---|
| 1 | Understanding Password Security: Hashing Algorithms and Salting | Start → |
| 2 | Password Cracking Techniques: Brute-Force, Dictionary Attacks, Rainbow Tables | Start → |
| 3 | Using Password Cracking Tools: John the Ripper, Hashcat | Start → |
| 4 | Implementing Strong Password Policies | Start → |
| 5 | Multi-Factor Authentication (MFA) and its Importance | Start → |
| 6 | Hands-on: Cracking Weak Passwords | Start → |
Module 7: Web Application Security
| # | Topic | Link |
|---|
| 1 | Introduction to Web Application Security Risks | Start → |
| 2 | Common Web Application Vulnerabilities: OWASP Top 10 | Start → |
| 3 | Cross-Site Scripting (XSS) Attacks and Prevention | Start → |
| 4 | SQL Injection Attacks and Prevention | Start → |
| 5 | Authentication and Authorization Vulnerabilities | Start → |
| 6 | Session Management Vulnerabilities | Start → |
| 7 | Hands-on: Identifying and Exploiting Web Application Vulnerabilities | Start → |