India’s Unrest in 2025: Protests, Politics, and Media Coverage Amid Regional Tensions
IntroductionAs India navigates 2025, a wave of protests has swept across states, from Bihar’s electoral battles to Assam’s ethnic demands, fueled by grievances over voter rights, jobs, farmers’ woes, and…
Generative AI and Angetic System: 7 Powerful Insights Transforming Technology
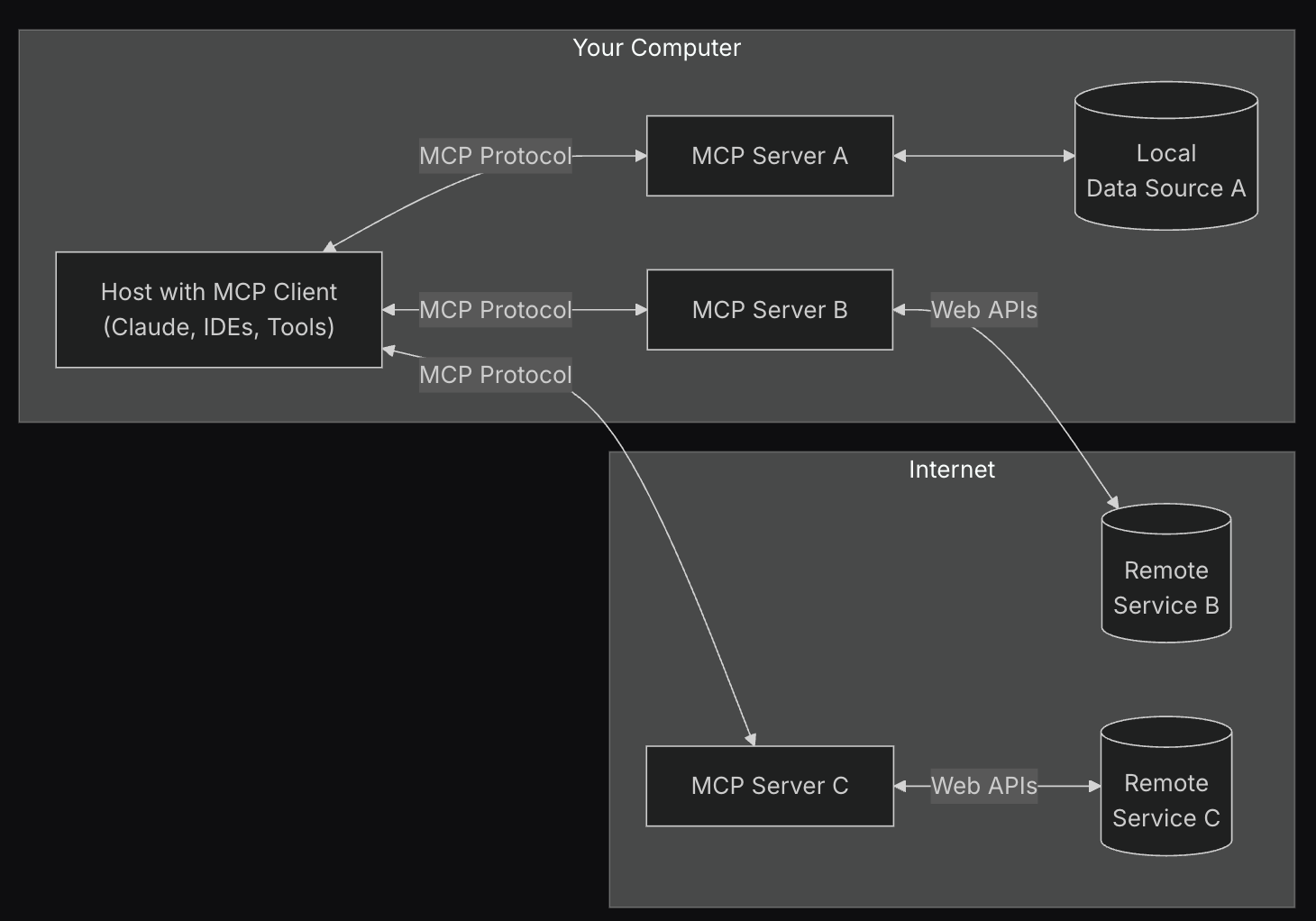
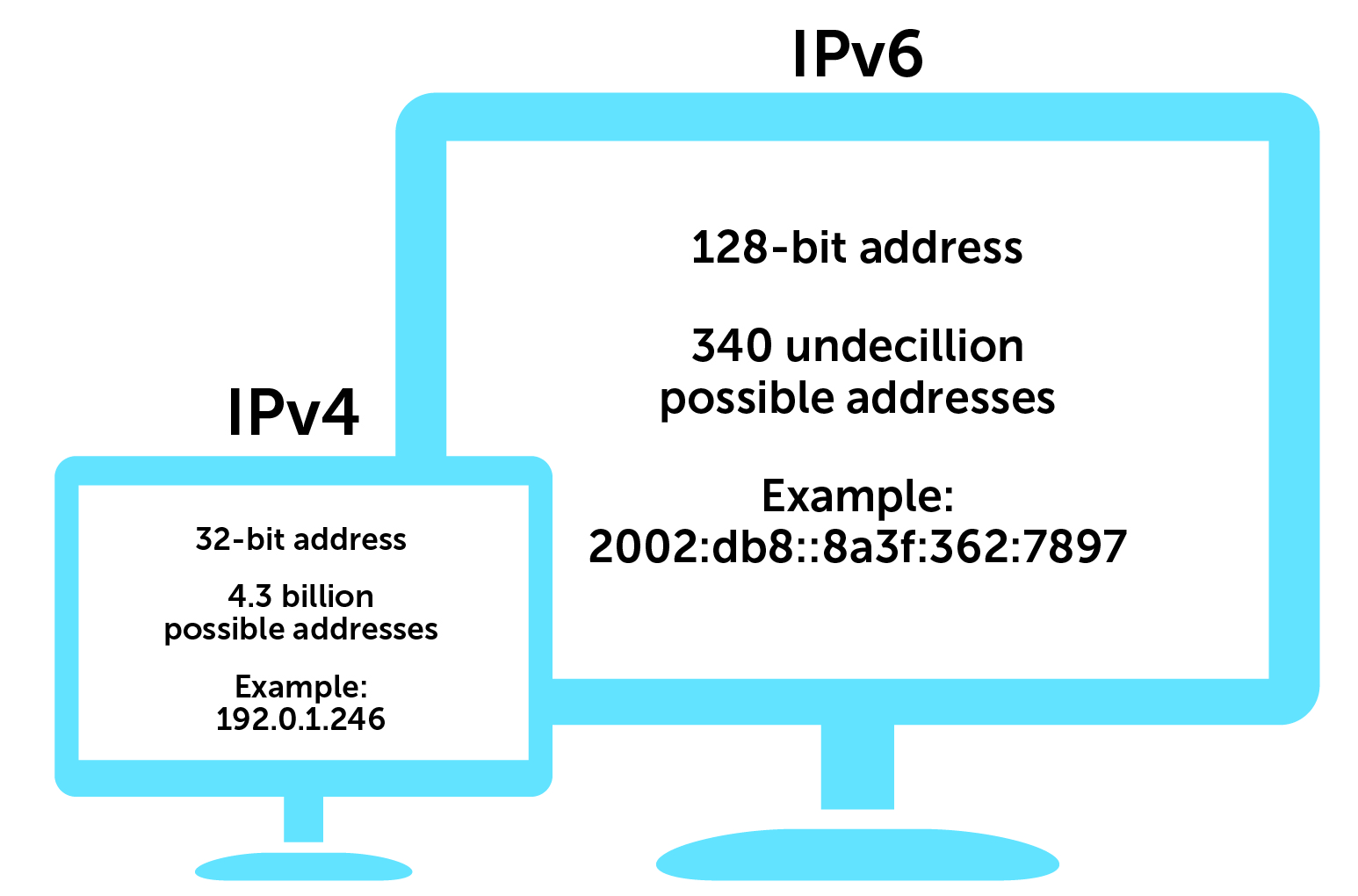
Introduction Artificial Intelligence (AI) is evolving at an unprecedented pace, and two concepts are now shaping the frontier: Generative AI and Angetic System. Generative AI has captured global attention for…
GAN Structure: A Complete Guide to Generative Adversarial Networks
Generative Adversarial Networks (GANs) have rapidly become one of the most innovative breakthroughs in artificial intelligence. From generating ultra-realistic images to advancing medical research, GANs are transforming industries with their…
Mastering Vibe Coding: The Future of Creative and Technical Synergy
In today’s rapidly evolving digital era, vibe coding has emerged as a powerful concept that bridges the gap between creativity and technical innovation. By combining human intuition, emotional intelligence, and…
Are Philips Hue Essential bulbs the cheap smart lights we don’t need?
There’s no shortage of brands making affordable smart lights, but it looks like Hue wants a piece of the entry-level pie. There’s no shortage of brands making affordable smart lights,…
The Casabrews 5418 Pro is a super-affordable espresso machine, but too many corners have been cut to make it a good budget buy
The 5418 Pro has an appealing price tag, but the more I used it, the more the compromises became apparent. The 5418 Pro has an appealing price tag, but the…
I’ve tested 14 coffee makers in the last year, and these are my 3 favorite budget-friendly options
You can easily spend hundreds on a coffee maker – but you don’t have to. You can easily spend hundreds on a coffee maker – but you don’t have to.
I’ve been eyeing the De’Longhi La Specialista Touch espresso machine – and now it’s got a 22% discount
The De’Longhi La Specialista Touch is a fantastic bean-to-cup espresso machine for coffee novices and experts alike, and it’s now received a huge discount at eBay. The De’Longhi La Specialista…
Smeg’s new Mini Milk Frother prepares perfect foam for cappuccinos – but it’s too thick for latte art
Smeg’s super-compact frother is whisper-quiet and super simple to use, but only offers one foam texture, and it’s seriously thick. Smeg’s super-compact frother is whisper-quiet and super simple to use,…
This quiet but powerful pedestal fan blew me away during testing – here’s why I’ve rated it 5 stars
Strong yet surprisingly quiet, this versatile air circulator has me seriously impressed. Strong yet surprisingly quiet, this versatile air circulator has me seriously impressed.

 India’s Unrest in 2025: Protests, Politics, and Media Coverage Amid Regional Tensions
India’s Unrest in 2025: Protests, Politics, and Media Coverage Amid Regional Tensions Generative AI and Angetic System: 7 Powerful Insights Transforming Technology
Generative AI and Angetic System: 7 Powerful Insights Transforming Technology GAN Structure: A Complete Guide to Generative Adversarial Networks
GAN Structure: A Complete Guide to Generative Adversarial Networks Mastering Vibe Coding: The Future of Creative and Technical Synergy
Mastering Vibe Coding: The Future of Creative and Technical Synergy Are Philips Hue Essential bulbs the cheap smart lights we don’t need?
Are Philips Hue Essential bulbs the cheap smart lights we don’t need? The Casabrews 5418 Pro is a super-affordable espresso machine, but too many corners have been cut to make it a good budget buy
The Casabrews 5418 Pro is a super-affordable espresso machine, but too many corners have been cut to make it a good budget buy I’ve tested 14 coffee makers in the last year, and these are my 3 favorite budget-friendly options
I’ve tested 14 coffee makers in the last year, and these are my 3 favorite budget-friendly options I’ve been eyeing the De’Longhi La Specialista Touch espresso machine – and now it’s got a 22% discount
I’ve been eyeing the De’Longhi La Specialista Touch espresso machine – and now it’s got a 22% discount Smeg’s new Mini Milk Frother prepares perfect foam for cappuccinos – but it’s too thick for latte art
Smeg’s new Mini Milk Frother prepares perfect foam for cappuccinos – but it’s too thick for latte art This quiet but powerful pedestal fan blew me away during testing – here’s why I’ve rated it 5 stars
This quiet but powerful pedestal fan blew me away during testing – here’s why I’ve rated it 5 stars