Common Network Protocols: HTTP, HTTPS, DNS, SMTP
Understanding network protocols is crucial for ethical hackers. These protocols are the languages that devices use to communicate, and knowing how they work allows you to identify vulnerabilities and potential…
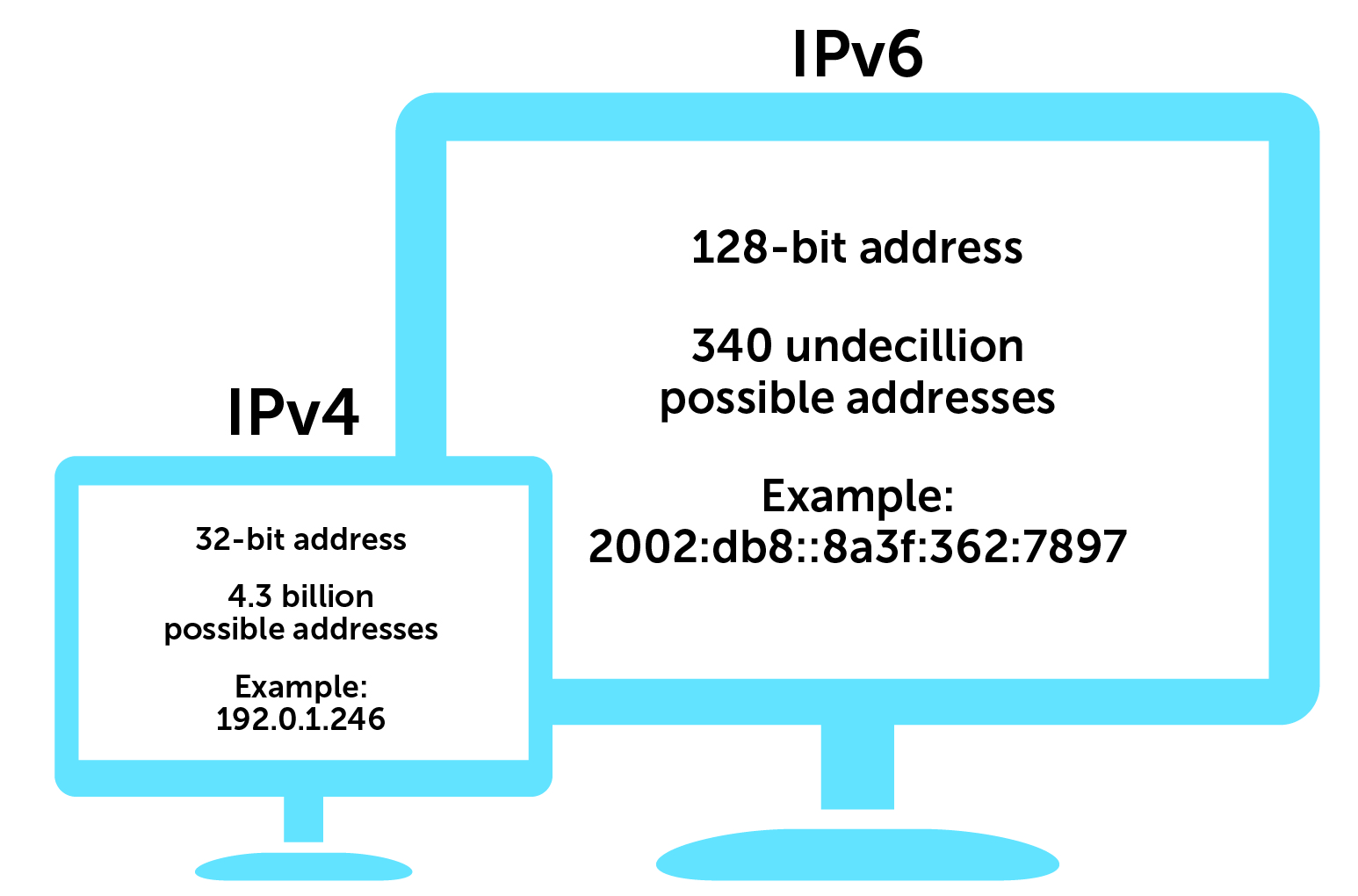
Understanding IP Addressing: IPv4 and IPv6
IP addressing is the backbone of network communication, enabling devices to identify and locate each other on a network. Understanding IP addresses, both IPv4 and IPv6, is crucial for ethical…
Crypto Mogul’s Faked Death Triggers Memecoin Chaos: The Rise and Fall of LLJEFFY
The Staged Suicide and Viral Memecoin SurgeOn May 4, 2025, Zerebro co-founder Jeffy Yu, a 23-year-old crypto entrepreneur, appeared to take his own life during a livestream on Pump.fun, a…
Introduction to Networking Concepts: TCP/IP Model, OSI Model
Networking is the backbone of modern communication and a critical area for ethical hackers to understand. A solid grasp of networking concepts allows you to identify vulnerabilities, analyze network traffic,…
MEXC Lists Doodles (DOOD) with 50,000 USDT Worth of DOOD and 50,000 USDT Bonus Prize Pool
The cryptocurrency exchange MEXC has made waves in the Web3 space with its May 9, 2025, listing of Doodles (DOOD), the native token of the beloved NFT-turned-entertainment brand Doodles. This move…
What is Software Architecture?
Software architecture is the fundamental organization of a software system, encompassing its components, their relationships to each other and to the environment, and the principles guiding its design and evolution.…
India-Pakistan Conflict: Live Updates on Military Strikes and Escalating Tensions
IntroductionTensions between India and Pakistan have reached a critical point following a deadly terror attack in Pahalgam, Jammu and Kashmir, on April 22, 2025, which claimed 26 lives, mostly tourists.…
Setting up a Virtual Lab Environment for Ethical Hacking
Setting up a virtual lab environment is a crucial first step in learning ethical hacking. It provides a safe and isolated space to experiment with tools and techniques without risking…
Common Cybersecurity Threats: Malware, Phishing, and Social Engineering
Malware, phishing, and social engineering represent some of the most pervasive and dangerous threats in the cybersecurity landscape. Understanding how these attacks work, how to recognize them, and how to…
The Ethical Hacker’s Code of Ethics and Legal Considerations
The ethical hacker’s role is critical in safeguarding digital assets, but this role comes with significant responsibilities. Understanding and adhering to a strict code of ethics and being aware of…